Difference between revisions of "Unofficial guide to MTDBG"
Nisargshah95 (talk | contribs) m (→bpm: changed 'bpm w' to 'bpmw') |
|||
| (8 intermediate revisions by one other user not shown) | |||
| Line 7: | Line 7: | ||
MTDBG is the application-level debugger for KolibriOS. <br> | MTDBG is the application-level debugger for KolibriOS. <br> | ||
It can make your life easier on many occasions. Whether you are still learning assembly and just want to see what's going on, or you are trying to fix that bug that nobody else has the guts for. | It can make your life easier on many occasions. Whether you are still learning assembly and just want to see what's going on, or you are trying to fix that bug that nobody else has the guts for. | ||
| + | |||
| + | = Overview = | ||
| + | |||
| + | [[Image:Mtdbg_overview.png]] | ||
= Loading your application = | = Loading your application = | ||
| Line 23: | Line 27: | ||
In FASM on KolibriOS, select the 'generate debug information' check-box before assembling your code. <br> | In FASM on KolibriOS, select the 'generate debug information' check-box before assembling your code. <br> | ||
FASM will now create a *.dbg file in the same folder as the binary, which should be automatically loaded by MTDBG when loading the binary. | FASM will now create a *.dbg file in the same folder as the binary, which should be automatically loaded by MTDBG when loading the binary. | ||
| + | |||
| + | MTDBG versions 0.34 and newer also have support to load symbols from a .map file that can be generated by GCC. | ||
[[Image:Mtdbg1.png]] | [[Image:Mtdbg1.png]] | ||
| Line 47: | Line 53: | ||
=== load === | === load === | ||
Load the program you want to debug. <br> | Load the program you want to debug. <br> | ||
| − | <b> eg. 'load /rd/1/example' </b> | + | ''<b>eg. 'load /rd/1/example' </b> |
=== load-symbols === | === load-symbols === | ||
Load the debug symbols. <br> | Load the debug symbols. <br> | ||
These symbols can be generated with FASM on KolibriOS by selecting the 'generate debug symbols' option before compiling the code. <br> <br> The debug symbols have .dbg extension.<br> If the symbols exist in the same directory, and with the same filename as the binary, they will be loaded automatically.<br> | These symbols can be generated with FASM on KolibriOS by selecting the 'generate debug symbols' option before compiling the code. <br> <br> The debug symbols have .dbg extension.<br> If the symbols exist in the same directory, and with the same filename as the binary, they will be loaded automatically.<br> | ||
| − | <b> eg. 'load-symbols /rd/1/example.dbg </b> | + | ''<b>eg. 'load-symbols /rd/1/example.dbg </b> |
== controlling the view == | == controlling the view == | ||
| Line 59: | Line 65: | ||
Dump data at a given addres.<br> | Dump data at a given addres.<br> | ||
Parameter can be direct hex address, register or label.<br> | Parameter can be direct hex address, register or label.<br> | ||
| − | <b> eg. 'd esi' </b> | + | ''<b>eg. 'd esi' </b> |
=== u === | === u === | ||
Unassemble code at a given addres.<br> | Unassemble code at a given addres.<br> | ||
Parameter can be direct hex address, register or label.<br> | Parameter can be direct hex address, register or label.<br> | ||
| − | <b> eg. 'u redraw' </b> | + | ''<b>eg. 'u redraw' </b> |
== Stepping and running == | == Stepping and running == | ||
| Line 79: | Line 85: | ||
=== ? === | === ? === | ||
Calculate the value of an expression (and print the value to the debugger). <br> | Calculate the value of an expression (and print the value to the debugger). <br> | ||
| − | <b> eg. '? eax - ebx' </b> | + | ''<b>eg. '? eax - ebx'</b> |
=== r === | === r === | ||
Change the value of a register to a given expression. <br> | Change the value of a register to a given expression. <br> | ||
| − | <b> eg. 'r eax 1234'<br> | + | ''<b>eg. 'r eax 1234'<br> |
| − | eg. 'r eax edx'</b> | + | ''eg. 'r eax edx'</b> |
== breakpoints == | == breakpoints == | ||
| Line 91: | Line 97: | ||
Set a (regular) breakpoint. <br> | Set a (regular) breakpoint. <br> | ||
The debugger will suspend the debugged process whenever such a point is reached.<br> | The debugger will suspend the debugged process whenever such a point is reached.<br> | ||
| − | <b> eg. 'bp redraw' <br> | + | ''<b> eg. 'bp redraw'<br> |
| − | eg 'bp 1234'</b> | + | ''eg. 'bp 1234'</b> |
=== bpm === | === bpm === | ||
| Line 98: | Line 104: | ||
The debugger will suspend the debugged process when the data at the given address is being accessed. <br><br> | The debugger will suspend the debugged process when the data at the given address is being accessed. <br><br> | ||
You must give the size of the data type (b = byte, w = word, d = dword) and the type of access on which you want to break (r = read/write [default], w = write only)<br> | You must give the size of the data type (b = byte, w = word, d = dword) and the type of access on which you want to break (r = read/write [default], w = write only)<br> | ||
| − | <b> eg. ' | + | ''<b> eg. 'bpmw 1234'</b> |
=== bc === | === bc === | ||
Clear a breakpoint (remove it completely).<br> | Clear a breakpoint (remove it completely).<br> | ||
| − | <b> eg. 'bc 0'</b> | + | ''<b> eg. 'bc 0'</b> |
=== bd === | === bd === | ||
Disable a breakpoint (but remember the address in list).<br> | Disable a breakpoint (but remember the address in list).<br> | ||
| − | <b> eg. 'bd 1'</b> | + | ''<b> eg. 'bd 1'</b> |
=== be === | === be === | ||
Enable a previously disabled breakpoint.<br> | Enable a previously disabled breakpoint.<br> | ||
| − | <b>eg. 'be 0'</b> | + | ''<b>eg. 'be 0'</b> |
=== bl === | === bl === | ||
List all active breakpoints.<br> | List all active breakpoints.<br> | ||
| + | = Expressions = | ||
| + | |||
| + | Some of the previously listed commands accept so called expressions as an input. <br> | ||
| + | Expressions can include: | ||
| + | * Hexadecimal constants. | ||
| + | * Names of general-purpose registers. | ||
| + | * +, -, *, / arithmetic symbols (with standard priorities) and brackets. | ||
| + | * labels from symbol file. | ||
| + | |||
| + | some examples:<br> | ||
| + | <b> | ||
| + | '' eax <br> | ||
| + | '' eip+2 <br> | ||
| + | '' ecx-esi-1F <br> | ||
| + | '' al+ah*bl <br> | ||
| + | '' ax+2*bh*(eip+ a73) <br> | ||
| + | '' *esi*di/eax <br> | ||
| + | </b> | ||
| + | |||
| + | = User breakpoints = | ||
| + | |||
| + | Another way of inserting breakpoints into the program you want to debug, is by putting them inside the binary. <br> | ||
| + | This can be done with a hex editor, your assembler, or even your compiler. <br> | ||
| + | MTDBG will recognize all "int 3" instructions as so called user breakpoints. So all you need to do is place "int 3" assembly code at the place where you'd like the program to halt for inspection. (Or you can try to be hardcore and just use 0xCC hexadecimal code.) | ||
[[Category:Coding]] | [[Category:Coding]] | ||
Latest revision as of 11:35, 11 July 2016
Disclaimer
This is an unofficial guide, targetted at the beginner. The official documentation is called 'mtdbg.txt' and can be found in DOCPACK program in KolibriOS.
Using MTDBG
MTDBG is the application-level debugger for KolibriOS.
It can make your life easier on many occasions. Whether you are still learning assembly and just want to see what's going on, or you are trying to fix that bug that nobody else has the guts for.
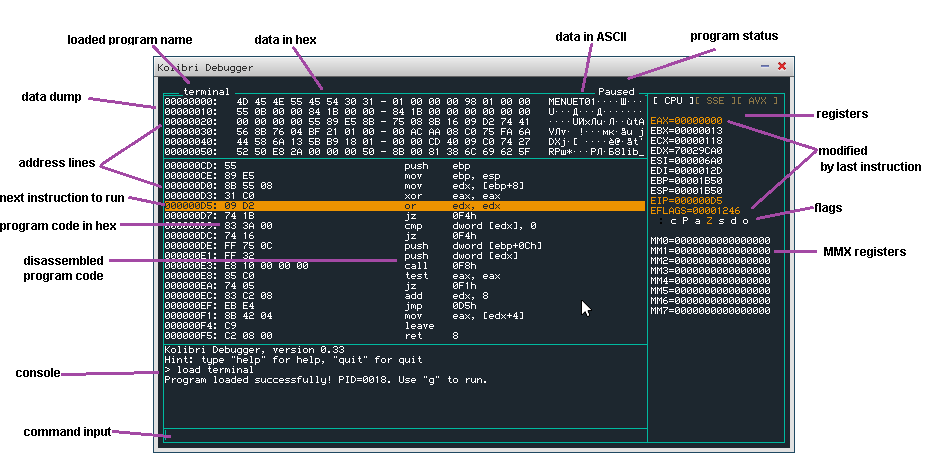
Overview
Loading your application
There are several ways to load your application into the debugger.
You could simply click 'MTDBG' icon on the KolibriOS desktop and use the 'load' command from there.
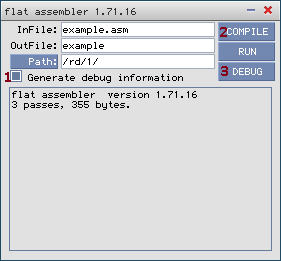
Another option is to load it from FASM (in KolibriOS) with 'debug' button.
The third option is to load directly from tinypad by pressing f10 or choosing "run > run in debugger" from the menu while your source code is opened in tinypad.
Loading symbols
The debugger works with binary code. It views the unassembled code to the developer, but this code has much less information then the original assembly code.
All information such as labels, comments etc. were lost during assembly process.
When working on a binary, this information cannot be recovered.
When you have the original source code however, it can be useful to load this information into the debugger so it displays the original label names additional to the hexadecimal addresses.
In FASM on KolibriOS, select the 'generate debug information' check-box before assembling your code.
FASM will now create a *.dbg file in the same folder as the binary, which should be automatically loaded by MTDBG when loading the binary.
MTDBG versions 0.34 and newer also have support to load symbols from a .map file that can be generated by GCC.
Using breakpoints
Single stepping can be really fun when you have nothing else to do, but most developers probably want to spend their time usefully.
Therefore, you can request the debugger to halt the execution of the program when a given instruction is about to be run.
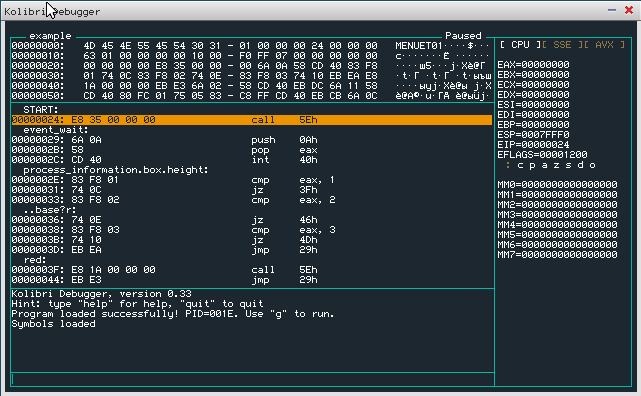
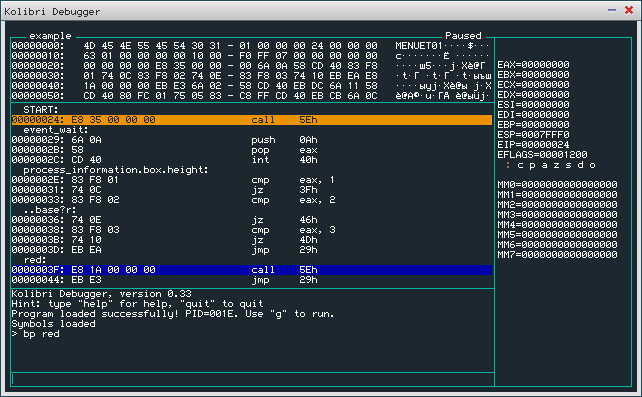
Lets assume we have our symbols loaded, and we are interested in what happens after the label 'red'.
(Offcourse you can also enter addresses in hexadecimal, when no symbols are loaded, or the instruction of interest has no label)
While the program is suspended (default state after loading a program), type 'bp red' to set the breakpoint.
You will see the label highlighted in blue in the disassembly view.
Now you can run the program (eg by using the command 'g') and the program will suspend when the subroutine of interest is reached.
Commands
loading files into the debugger
load
Load the program you want to debug.
eg. 'load /rd/1/example'
load-symbols
Load the debug symbols.
These symbols can be generated with FASM on KolibriOS by selecting the 'generate debug symbols' option before compiling the code.
The debug symbols have .dbg extension.
If the symbols exist in the same directory, and with the same filename as the binary, they will be loaded automatically.
eg. 'load-symbols /rd/1/example.dbg
controlling the view
d
Dump data at a given addres.
Parameter can be direct hex address, register or label.
eg. 'd esi'
u
Unassemble code at a given addres.
Parameter can be direct hex address, register or label.
eg. 'u redraw'
Stepping and running
s
Single step. Execute the following instruction and then halt.
g
Go on. (Resume execution of program)
Execution will terminate when a breakpoint is reached, the application exits or when there occurs a fault (divide by 0, page fault, ..)
reading/manipulating the registers
?
Calculate the value of an expression (and print the value to the debugger).
eg. '? eax - ebx'
r
Change the value of a register to a given expression.
eg. 'r eax 1234'
eg. 'r eax edx'
breakpoints
bp
Set a (regular) breakpoint.
The debugger will suspend the debugged process whenever such a point is reached.
eg. 'bp redraw'
eg. 'bp 1234'
bpm
Set a data breakpoint.
The debugger will suspend the debugged process when the data at the given address is being accessed.
You must give the size of the data type (b = byte, w = word, d = dword) and the type of access on which you want to break (r = read/write [default], w = write only)
eg. 'bpmw 1234'
bc
Clear a breakpoint (remove it completely).
eg. 'bc 0'
bd
Disable a breakpoint (but remember the address in list).
eg. 'bd 1'
be
Enable a previously disabled breakpoint.
eg. 'be 0'
bl
List all active breakpoints.
Expressions
Some of the previously listed commands accept so called expressions as an input.
Expressions can include:
- Hexadecimal constants.
- Names of general-purpose registers.
- +, -, *, / arithmetic symbols (with standard priorities) and brackets.
- labels from symbol file.
some examples:
eax
eip+2
ecx-esi-1F
al+ah*bl
ax+2*bh*(eip+ a73)
*esi*di/eax
User breakpoints
Another way of inserting breakpoints into the program you want to debug, is by putting them inside the binary.
This can be done with a hex editor, your assembler, or even your compiler.
MTDBG will recognize all "int 3" instructions as so called user breakpoints. So all you need to do is place "int 3" assembly code at the place where you'd like the program to halt for inspection. (Or you can try to be hardcore and just use 0xCC hexadecimal code.)